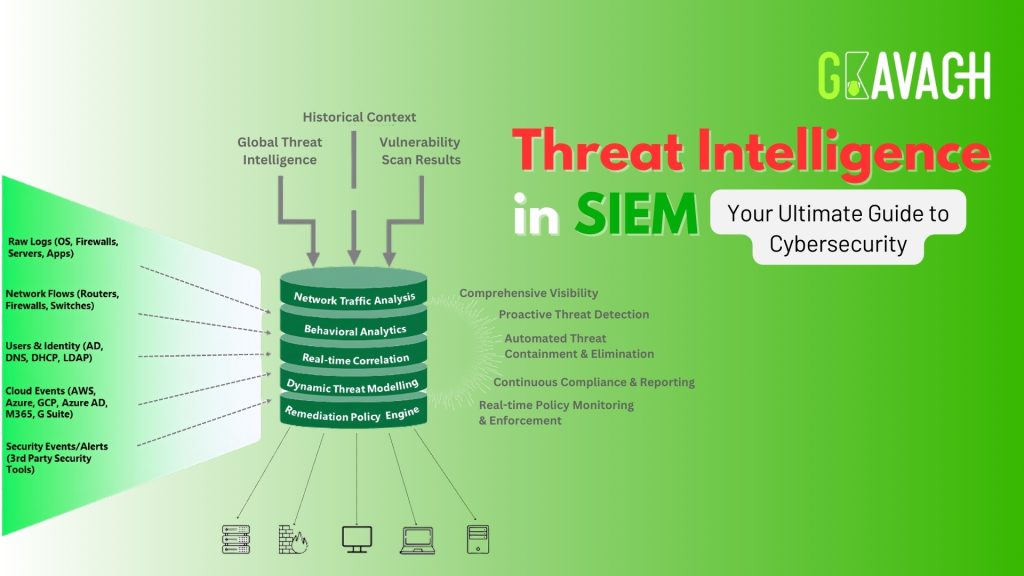
In today’s rapidly evolving threat landscape, cybersecurity is no longer just a nice-to-have, but a critical necessity. Cyberattacks are becoming increasingly sophisticated, targeting businesses of different sizes and industries. One powerful tool in your cybersecurity arsenal is the combination of threat intelligence and your Security Information and Event Management (SIEM) system. This dynamic duo can help you stay ahead of the curve, detect threats faster, and respond proactively to protect your organization’s valuable assets.
What is Threat Intelligence?
Think of threat intelligence as your organization’s early warning system for cyberattacks. It is the process of collecting, analyzing, and interpreting information about potential cyber threats, vulnerabilities, and malicious actors. This information can come from a variety of sources, including:
- Open-source intelligence: Publicly available information like news articles, security blogs, and forums.
- Commercial threat intelligence feeds: Subscription-based services that provide curated threat data from a variety of sources.
- Internal threat intelligence: Information gathered from your own systems and networks.
How Threat Intelligence Empowers Your SIEM
Your SIEM is already a powerful tool for collecting and analyzing security event data, but it becomes even more potent when combined with threat intelligence. Here’s how:
- Enhanced Threat Detection: Threat intelligence feeds enrich your SIEM with the latest information on known threats, indicators of compromise (IOCs), and attack patterns. This enables your SIEM to identify suspicious activity that might otherwise go unnoticed.
- Reduced False Positives: By correlating SIEM events with threat intelligence data, you can filter out harmless anomalies and focus your attention on the real threats. This reduces alert fatigue and saves valuable time and resources.
- Accelerated Incident Response: When a threat is detected, threat intelligence provides valuable context about the attack, helping you to understand its nature and scope. This enables you to respond quickly and effectively, minimizing damage and downtime.
- Proactive Security Posture: By staying informed about emerging threats and vulnerabilities, you can proactively strengthen your defenses before they are exploited. This reduces your organization’s overall risk profile.
Integrating Threat Intelligence Feeds
Integrating threat intelligence into your SIEM can be done through various methods:
- APIs: Many threat intelligence providers offer APIs that allow you to automate the ingestion of threat data into your SIEM.
- STIX/TAXII: The Structured Threat Information eXpression (STIX) and Trusted Automated eXchange of Indicator Information (TAXII) standards provide a common framework for sharing threat intelligence data.
- Manual Uploads: If you have limited resources, you can manually upload threat intelligence data into your SIEM, although this is not as efficient as automated methods.
Best Practices for Threat Intelligence in SIEM
To maximize the benefits of threat intelligence in your SIEM, follow these best practices:
- Define Clear Objectives: Determine what you want to achieve with threat intelligence. Are you primarily focused on threat detection, incident response, or proactive security?
- Choose the Right Feeds: Select threat intelligence feeds that are relevant to your industry, geographic location, and specific threats you face.
- Establish a Threat Intelligence Program: Create a formal program with dedicated resources to manage threat intelligence processes, including collection, analysis, and dissemination.
- Regularly Evaluate and Adjust: The threat landscape is constantly changing. Regularly review your threat intelligence feeds and adjust your strategy as needed.
Frequently Asked Questions
- What is the difference between open-source and commercial threat intelligence feeds?
Open-source feeds are freely available but may require more effort to curate and validate. Commercial feeds are paid subscriptions that often provide more comprehensive and verified data.
- How do I choose the right threat intelligence feeds for my organization?
Consider your industry, geographic location, and the specific threats you face. Look for feeds that offer relevant, timely, and actionable intelligence.
- Is it difficult to integrate threat intelligence into my SIEM?
The level of difficulty can vary depending on your SIEM platform and the threat intelligence provider. However, many providers offer APIs or pre-built integrations that simplify the process. For instance, GKavach, as a next-generation SIEM solution, provides integrated threat intelligence, eliminating the need for complex configurations or manual data ingestion. This means you can start leveraging the power of threat intelligence to enhance your security posture almost immediately.
- Can I use threat intelligence without a SIEM?
While a SIEM is not strictly necessary, it is highly recommended. A SIEM provides a centralized platform for collecting, analyzing, and correlating security data, making it easier to leverage threat intelligence effectively.
Conclusion
Threat intelligence is a vital component of any modern cybersecurity strategy. By integrating threat intelligence into your SIEM, you can significantly enhance your ability to detect, respond to, and prevent cyberattacks. This proactive approach will help safeguard your organization’s valuable assets and ensure business continuity in the face of evolving threats.