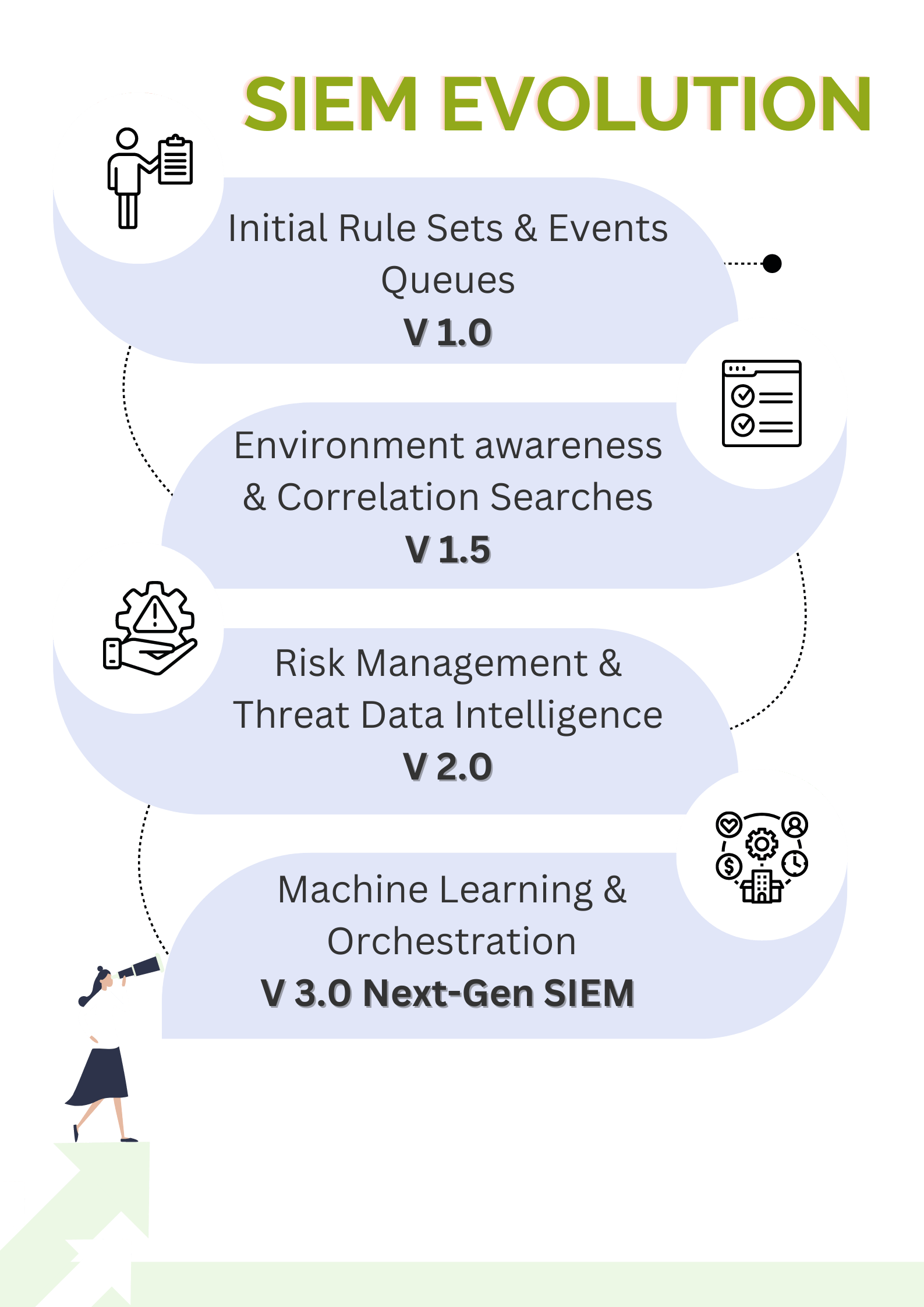
SIEM as a Service
Next-Gen SIEM Vs Traditional SIEM
SIEM as a Service
SIEM as a Service (SIEMaaS) is a security management solution that provides businesses with the benefits of a SIEM solution. SIEMaaS offers real-time threat detection, incident response, and log management, allowing businesses to stay ahead of cyber threats. With SIEMaaS, businesses can collect, analyze, and correlate security events from various sources across their network, including firewalls, servers, endpoints, and applications. SIEMaaS also provides advanced analytics and machine learning algorithms that can detect and respond to threats faster than traditional SIEM solutions.
How Can Gkavach SIEM as a Service Benefit Your Business?
Simplified Management
With Gkavach SIEM as a service, the provider manages the infrastructure and technology required for security monitoring, freeing up your IT staff to focus on other critical areas of the business.
Scalability
Gkavach's solution is highly scalable, making it an ideal solution for businesses of all sizes. Whether you are a small startup or a large enterprise, Gkavach can scale its solution to meet your specific needs, without requiring you to invest in additional hardware or software.
Enables Compliance with Regulatory Standards
Gkavach SIEM as a service helps your organization meet regulatory compliance requirements by providing real-time monitoring and reporting capabilities.
Cost savings
Gkavach's solution can help businesses save on costs by eliminating the need for upfront capital expenditure on hardware, software, and IT staff. Additionally, Gkavach's solution is designed to provide cost-effective threat detection and response capabilities, reducing the costs associated with data breaches, downtime, and reputational damage.
Deployment Process of GKavach
The deployment process of Security Information and Event Management (SIEM) systems can differ depending on whether they are deployed on-premises or in the cloud. Here is a general overview of the deployment process for both scenarios:
On-Premises Deployment Process
- Identify Use Cases: Define the use cases for SIEM deployment based on the organization’s security needs.
- Plan Infrastructure: Identify the infrastructure requirements for deploying SIEM on-premises, such as hardware, software, network, and storage.
- Install and Configure SIEM: Install and configure the SIEM software on the designated hardware. Configure data sources to collect data from various sources such as servers, network devices, and applications.
- Tune the System: Fine-tune the system to minimize false positives and improve the accuracy of threat detection.
- Test and Validate: Perform testing and validation to ensure that the SIEM system is working correctly and is providing the desired results.
Cloud Deployment Process
- Provision Infrastructure: Provision the required infrastructure in the cloud provider’s environment, such as virtual machines, storage, and networking.
- Configure SIEM: Configure the SIEM system in the cloud provider’s environment. This includes configuring data sources, integration with other security tools, and tuning the system.
- Install Agents: Install agents on the data sources to collect data and send it to the SIEM system.
- Test and Validate: Perform testing and validation to ensure that the SIEM system is working correctly and is providing the desired results.