In the evolving world of cybersecurity, the ability to effectively parse and analyze logs is fundamental to any security strategy. Logs, which contain valuable data on system activities, network traffic, user behaviors, and more, are the cornerstone of security operations. However, as cyber threats become more sophisticated, traditional methods of log parsing have shown their limitations, making way for the rise of Next-Generation Security Information and Event Management (Next-Gen SIEM) systems. These systems provide enhanced capabilities for log collection, parsing, and analysis, thereby enabling better threat detection, faster incident response, and more efficient compliance management.
The Role of Logs in Security Monitoring
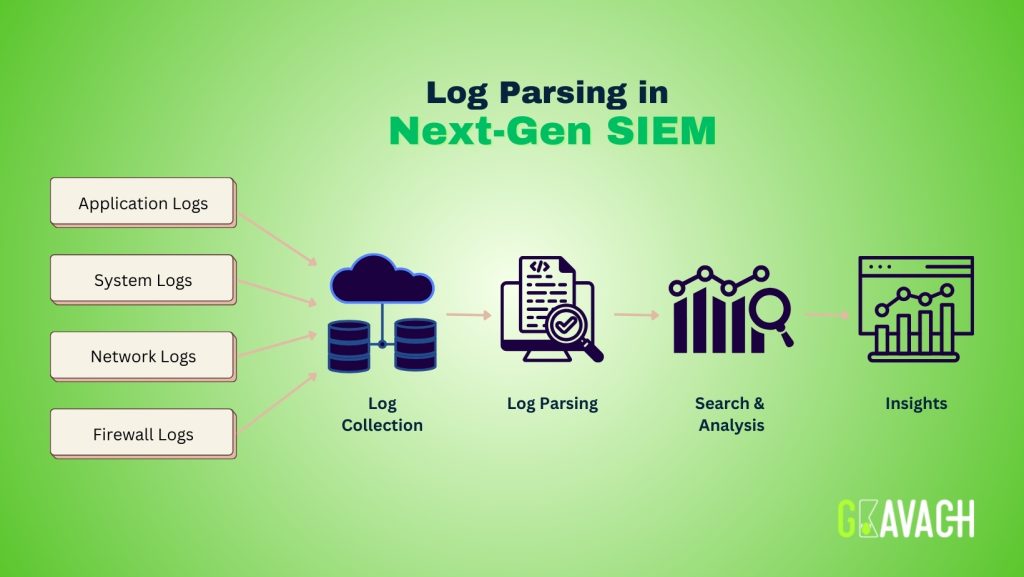
Logs are crucial for monitoring infrastructure, providing insights into system operations, user actions, and potential security breaches. Traditional SIEM systems used these logs for threat detection, but as enterprises move to complex, multi-cloud environments, the volume and diversity of logs have grown, driving the need for Next-Gen SIEM technology to handle these more complex data sets.
Traditional Log Collection and Parsing
In traditional environments, logs are collected from devices like servers, firewalls, and applications, often stored in plain text or proprietary formats. These logs are gathered using agents, parsed with predefined rules to extract patterns like timestamps or IP addresses, and normalized into a standard format for easier analysis. This process is rigid, resource-intensive, and error-prone, requiring manual configuration. Finally, the data is stored in a central repository for querying and reporting.
The Transition to Next-Gen SIEM
Next-Gen SIEM systems take traditional log parsing and processing a step further by incorporating advanced technologies such as machine learning, artificial intelligence (AI), and behavioral analytics. These systems are designed to handle not only an increasing volume of data but also the variety and complexity of modern IT environments, which include on-premise systems, cloud infrastructures, IoT devices, and mobile endpoints.
1. Automated Log Parsing and Enrichment
A key advancement in Next-Gen SIEM is the automation of log parsing. Unlike traditional systems, which rely on static rules, Next-Gen SIEM platforms use AI to automatically detect and parse logs from new or unknown sources, identifying patterns like IP addresses and timestamps without manual intervention. These systems can also enrich logs with threat intelligence, geolocation data, and user information, adding context for more effective threat detection and investigation.
2. Real-time Parsing and Streamlined Data Processing
Traditional SIEM systems struggle with real-time data processing as log volumes grow. In contrast, Next-Gen SIEM systems are designed for real-time log parsing, enabling immediate threat detection. Their advanced data pipelines handle high throughput and low latency, ensuring quick parsing and normalization even under heavy data loads.
3. Dynamic Parsing Models
Traditional SIEM systems are limited by rigid parsing rules that must be manually updated whenever new log sources or formats are introduced. In contrast, Next-Gen SIEM systems use dynamic parsing models that can adapt to new formats and sources in real-time. This means that as an organization introduces new systems or applications, the SIEM system can automatically recognize and process the logs without requiring manual intervention.
4. Machine Learning and Behavioral Analytics
Machine learning and behavioral analytics are used by next-generation SIEM solutions to improve detection. By learning from past incidents and user behavior, the system flags deviations from normal activity as potential threats. For example, if a user logs in from an unfamiliar location or accesses sensitive data outside normal hours, the system generates an alert, even if the logs seem harmless.
5. Cloud and Multi-Environment Support
As organizations move toward hybrid and multi-cloud environments, the complexity of managing logs from different sources increases. Next-Gen SIEM systems are designed to handle logs from a variety of environments—on-premise, public cloud, private cloud, and hybrid setups—without needing separate systems or manual configurations. This makes it easier for organizations to manage logs in a centralized way, regardless of where the data resides.

Real-World Application: How Logs are Automatically Analyzed, Parsed, and Visualized
Next-Gen SIEM systems bring enhanced capabilities for log analysis that traditional SIEM systems simply cannot achieve. Let’s explore a practical example to illustrate this transformation:
Traditional Log Example: Consider a log entry from a web server that simply logs a failed login attempt:
2024-11-07 12:05:01 192.168.1.1 TCP 192.168.1.5 443 DENY
In traditional SIEM, logs are parsed using predefined rules to identify fields like timestamps, IP addresses, and event types. However, it struggles to detect larger patterns or the behavior behind events, such as identifying a failed login attempt as part of a brute-force attack without manual effort.
Next-Gen SIEM After Parsing and Enrichment: Next-Gen SIEM automatically detects and processes this log, and adds valuable context:
Timestamp: 2024-11-07 12:05:01
Source IP: 192.168.1.5 (Location: USA, Threat Intelligence: Known Botnet)
Destination IP: 192.168.1.1 (Internal Server)
Action: DENY
Event Type: Firewall Block
Context: Multiple failed login attempts from the same IP in the last 5 minutes
Alert: Possible Brute Force Attack
In this example, Next-Gen SIEM enriches the log with machine learning and threat intelligence, identifying the source IP as part of a botnet and flagging the event as a possible brute-force attack, which traditional SIEM would struggle to analyze automatically.
Visualizing Logs and Making Charts
Next-Gen SIEM enhances log analysis by enabling real-time data visualization. Unlike traditional SIEM, which presents logs in raw or tabular form, Next-Gen SIEM displays logs through graphs and charts, making it easier to spot trends and patterns. For example, failed login attempts can be shown in a time-series graph, helping security teams quickly identify potential security threats and respond faster.
Conclusion
The evolution of SIEM technology has revolutionized log management. While traditional SIEM systems are limited, Next-Gen SIEM, with AI-driven parsing, real-time detection, and advanced visualization, improves threat detection, accelerates response times, and scales security management. As cyber threats evolve, organizations will increasingly rely on these advanced systems to protect their infrastructure.